PASSIVE DAST
We will
scan:

Certificates
-
Expiration
-
SSL issues
Domains
-
Zone transfer
-
Take over
-
Expiration
-
Email (SPF, DMARC & DKIM)


You will find you critical vulnerabilities & security threats with our Deep Scanning Process

You can also add another assets, like repositories, websites, servers...

With the initial assets from point 1, our tool will search & load all the possible assets.

Using all the assets found in point 2, our tool will do security checks that will generate Findings

Found vulnerabilities are notified in Slack & you can also check it in your user space, so you can work to fix them.

Discover all your public online assets by using our combination of different sophisticated reconnaissance techniques. See what attackers see.
We discover the assets in:
Test the security of your assets with the latest vulnerabilities and attack vectors in a continuous and automated way.
Our platform uses CVE, CWE & CVSS enumeration to reference the kind of vulnerabilities & it's severity, following the industry standards.
We are constantly updating our databases, so if you get a new vulnerability, you will find it quickly!
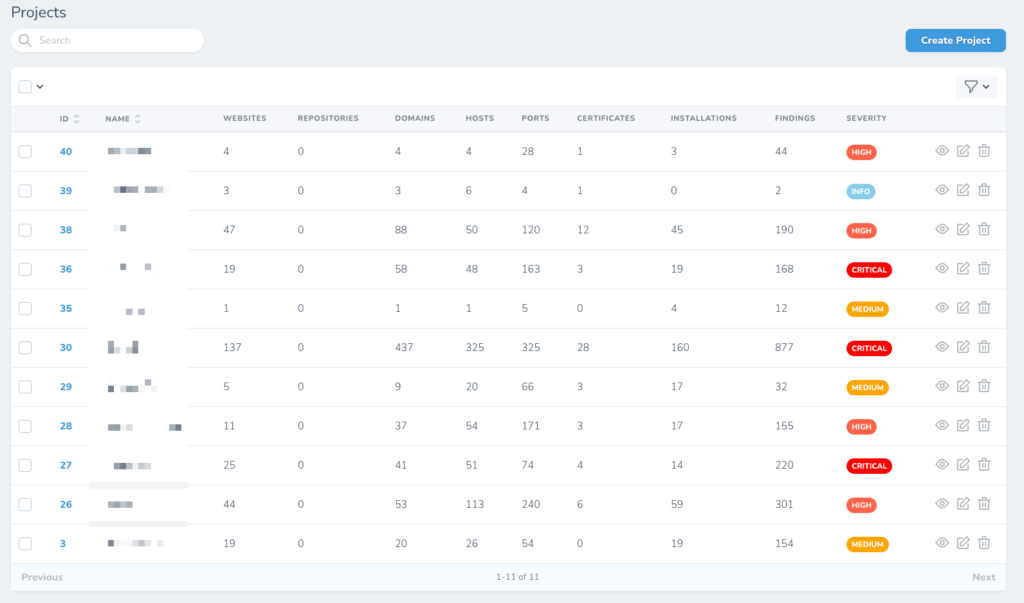

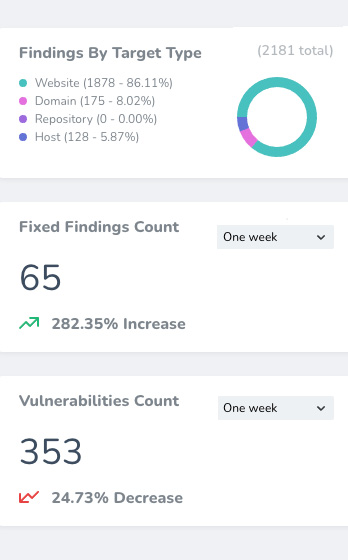
Manage all the findings categorized by its severity and focus on what really matters. Findings will automatically be mark as resolved once they are fixed.
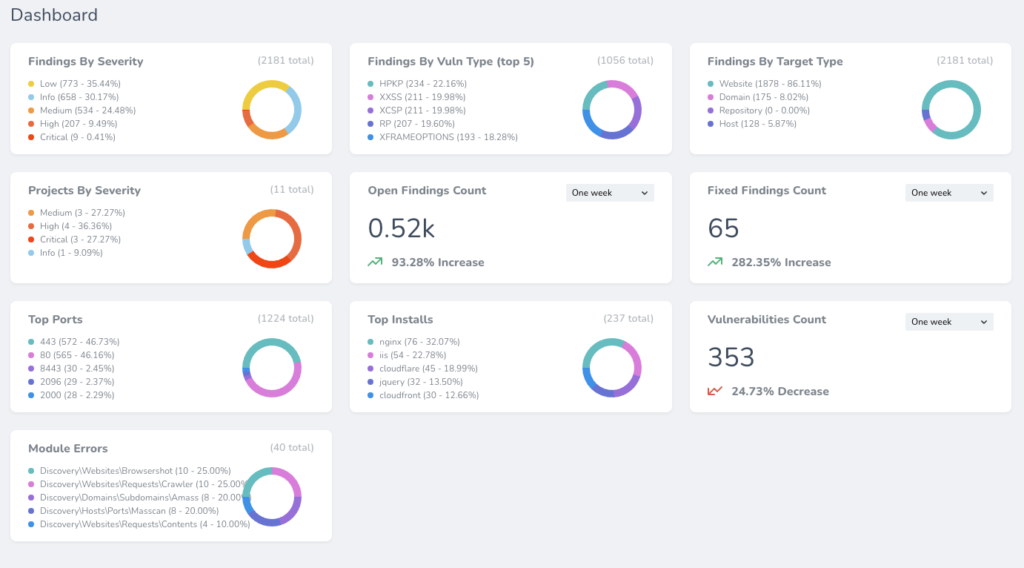

Export audit reports automatically in PDF or HTML for easy security compliance in the click of a button.
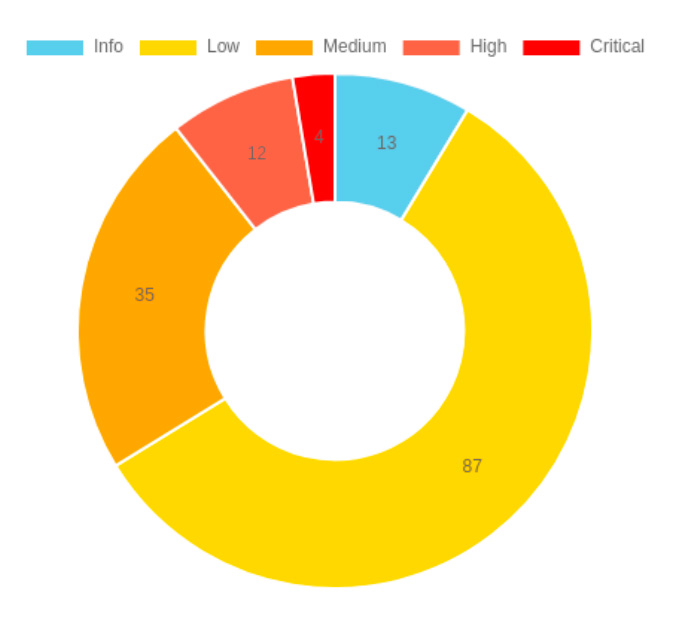
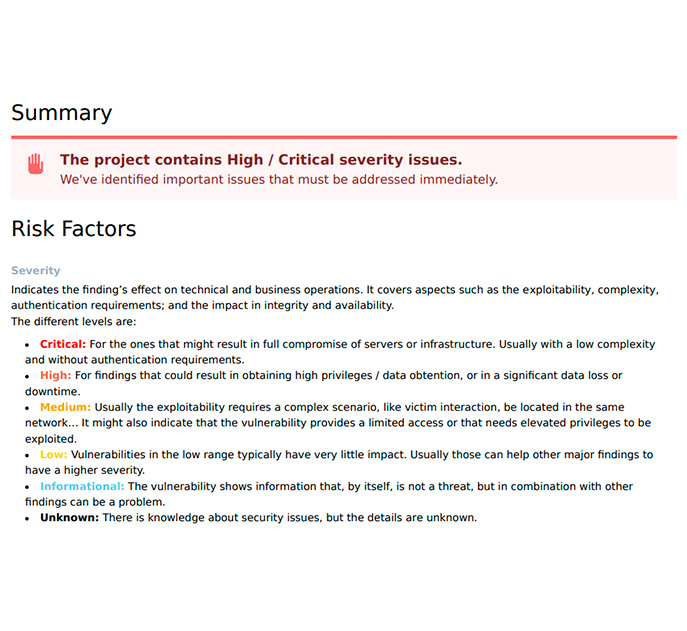
We have two kinds of Dynamic scanning for finding all the vulnerabilities and security threats.
PASSIVE DAST


ACTIVE DAST



Dependency vulnerabilities
Copyright 2024 FlowScan – All rights reserved